In the ever-evolving digital landscape, security threats are a constant concern. One such threat is a replay attack, which can compromise the integrity of data and transactions. In this blog post, we will delve into what is replay attack, the concept of replay attacks, understand how they work, examine an example, and explore strategies to prevent them.
Table of Contents
What is Replay Attack?
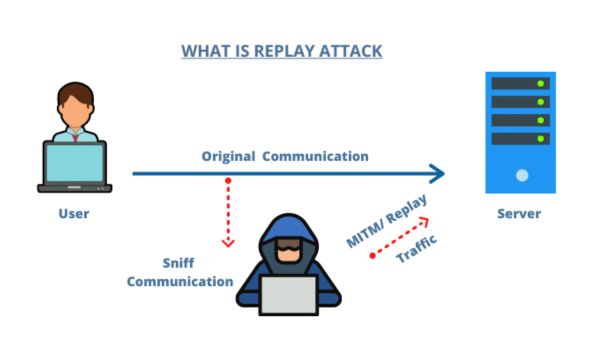
What is Replay Attack? A replay attack is a type of cyber attack where an attacker intercepts and maliciously replays valid data transmissions between two parties. The aim of a replay attack is to deceive the recipient into accepting a repeated or unauthorized transaction or message, leading to potential security breaches, financial loss, or unauthorized access.

How Would a Replay Attack Work?
To better understand how a replay attack works, let's consider a scenario involving a secure online transaction. Suppose you are making a purchase from an online store. During the transaction, sensitive data such as your credit card information is transmitted to the store's server securely. However, if an attacker manages to intercept this data, they can replay it later to deceive the server into accepting the same transaction multiple times.
The attacker can capture the encrypted data packets and resend them at a later time, bypassing any time-sensitive security measures in place. The server, unaware that the data has been replayed, may consider it legitimate and execute the transaction again, leading to financial loss or other adverse consequences.
Example of Replay Attack
Let's consider an example of a replay attack in the context of a smart door lock system. Imagine you have a smart lock installed on your front door, which allows you to unlock the door remotely using a smartphone app. The app communicates with the lock's server to send the unlock command securely.
Now, if an attacker eavesdrops on the communication between your smartphone and the lock's server and captures the encrypted unlock command, they can replay it at a later time. This would trick the lock's server into unlocking the door, granting unauthorized access to your home, even though you did not initiate the command.
What are the consequences of replay attack?
A replay attack is a type of cryptographic attack that can occur when a transaction or data from one blockchain network is maliciously or inadvertently copied and replayed on another blockchain network that shares a similar protocol or structure. The consequences of a replay attack can be significant and may include:
- Unauthorized Transactions: A successful replay attack can result in unauthorized transactions being executed on a different blockchain network. This can lead to unintended transfers of assets or tokens, causing financial loss or disruption to users and the affected blockchain network.
- Double Spending: In the context of cryptocurrency, a replay attack can enable double spending, where the same tokens or coins are spent multiple times. This can undermine the integrity and trustworthiness of the affected blockchain network, as it violates the core principle of ensuring that each transaction is unique and cannot be duplicated.
- Loss of Funds: If a replay attack is used to transfer funds from one network to another without proper authorization, it can result in the loss of funds for the victim. Once the transaction is replayed on the other network, the tokens or coins may be irreversibly transferred to the attacker's control.
- Network Disruption: Replay attacks can disrupt the affected blockchain network's operations and create confusion among users and participants. It can lead to transaction failures, delays, or inconsistencies, causing inconvenience and eroding trust in the network's reliability.
- Reputation Damage: A successful replay attack can damage the reputation of the affected blockchain network, especially if the attack exploits vulnerabilities or weaknesses that could have been prevented. Users may lose confidence in the network's security and integrity, leading to a loss of adoption and diminished market trust.
- Regulatory and Compliance Issues: Replay attacks can attract regulatory attention and scrutiny, as they can violate laws or regulations related to financial transactions or digital assets. Affected blockchain networks may face legal consequences or regulatory actions, potentially impacting their operations and market viability.
To mitigate the risk of replay attacks, blockchain networks and users can employ various preventive measures, such as implementing replay protection mechanisms, unique transaction identifiers, or protocol upgrades. Additionally, users should exercise caution when transacting across different blockchain networks, especially when networks share similar protocols or structures.
How to Prevent Replay Attacks

Preventing replay attacks requires a combination of robust security measures and best practices. Here are some effective strategies to consider:
- Message Authentication Codes (MAC): Implementing MACs can help prevent replay attacks. A MAC is a cryptographic technique that ensures the integrity and authenticity of a message by appending a unique signature or code to each transmitted message. This prevents attackers from replaying intercepted messages as the MAC will not match.
- Timestamps and Nonces: Including timestamps and nonces (a unique number used only once) in transmitted messages can prevent replay attacks. The recipient can verify the freshness of the message by comparing the timestamp and nonce with the current time and previously received nonces. If the message is too old or the nonce has been used before, it can be rejected.
- Secure Session Protocols: Utilize secure session protocols like Transport Layer Security (TLS) or Secure Sockets Layer (SSL) to establish encrypted connections between parties. These protocols provide data confidentiality, integrity, and authenticity, making it more challenging for attackers to intercept and replay messages.
- Challenge-Response Mechanisms: Implementing challenge-response mechanisms can add an extra layer of security against replay attacks. This involves the sender generating a unique challenge, and the recipient providing the correct response based on a pre-shared secret or cryptographic function. The response is then verified by the sender, ensuring the authenticity of the message.
- One-Time Passwords (OTPs): Implementing one-time passwords can be an effective preventive measure. OTPs are unique codes that are valid for a single use or a short period. By using OTPs for sensitive transactions or access control, the risk of replay attacks is significantly reduced.
- Message Sequencing and Tracking: Including message sequencing and tracking mechanisms in the communication protocol can help identify and reject replayed messages. Each message can have a sequence number or identifier that the recipient verifies to ensure the message is received in the correct order and has not been replayed.
Replay attacks pose a significant threat to data integrity, transaction security, and user privacy. Understanding what is replay attack, how replay attacks work and adopting preventive measures is crucial to safeguarding sensitive information. By implementing techniques such as message authentication codes, timestamps, secure session protocols, challenge-response mechanisms, one-time passwords, and message sequencing, individuals and organizations can fortify their defenses against replay attacks and mitigate potential risks in the digital landscape. Stay vigilant, stay secure! Let's go with Unicorn Ultra to follow the latest information on the market.