Blockchain technology relies on various consensus mechanisms, each tailored to validate and safeguard transactions in a decentralized network. One such standout method is Proof of Elapsed Time (PoET), which plays a pivotal role in achieving consensus within distributed ledgers. U2U Chain has incorporated PoET into its “Triple Layer Protection Mechanism.” This article thoroughly examines what is Proof of Elapsed Time, exploring its fundamental principles, advantages, drawbacks, and the positive impacts it has on U2U Chain.
Table of Contents
What is Proof of Elapsed Time (PoET)?
What is Proof of Elapsed Time (PoET)? Proof of Elapsed Time (PoET) stands out from other consensus mechanisms like Proof of Stake (PoS) or Proof of Work (PoW) due to its exclusive application in permissioned (private) blockchains, a departure from the open nature of permissionless counterparts such as Bitcoin and Ethereum. Unlike permissionless blockchains that welcome any node without prerequisites, permissioned blockchains demand personal identification from potential members, ensuring a pre-screened and trusted network. This meticulous selection negates the need for intricate trust validation methods for nodes, simplifying the process and enhancing computational efficiency.
PoET operates on the principle of equitable distribution of winning chances among the extensive network. It mimics a fair lottery system where every node enjoys an equal opportunity to win. To uphold this fairness, the system must satisfy three essential criteria:
- Random Waiting Time: Each node is assigned a random waiting period.
- Unbiased Selection: Nodes do not deliberately select the shortest waiting duration.
- Verification of Waiting Time Completion: The system verifies if a node has completed its designated waiting time.
Integral to PoET's functionality is Intel SGX (Software Guard Extensions), which plays a pivotal role by:
- Issuing Certificates: Providing nodes with certificates that validate their authenticity and integrity, ensuring their eligibility to generate new blocks within the network.
- Ensuring Trusted Code Execution: Verifying that nodes execute trusted code within a secure environment through a Trusted Execution Environment (TEE). This environment, shielded from external access, safeguards reserved and private storage areas, preventing inspection or alteration by other applications.

The development of PoET
In 2016, Intel, in partnership with the Linux Project and IBM, introduced the Hyperledger Sawtooth project, employing the PoET consensus mechanism. This innovation, designed to enhance the efficiency of enterprise applications such as supply chain and logistics, offers a scalable and flexible distributed ledger solution. The project aimed to mitigate the energy-intensive nature of the Proof of Work mining process while improving network performance.
How does PoET work?
In brief, PoET operates through four primary stages:
- Nodes in the network are allocated random waiting times.
- During this waiting period, nodes either sleep or perform other tasks.
- The node with the shortest waiting time awakens first and is authorized to create the block.
- After block production, the node shares the information with other participants in the network.
These four steps are categorized into two phases: the "Selection Process" and the "Genesis Process."
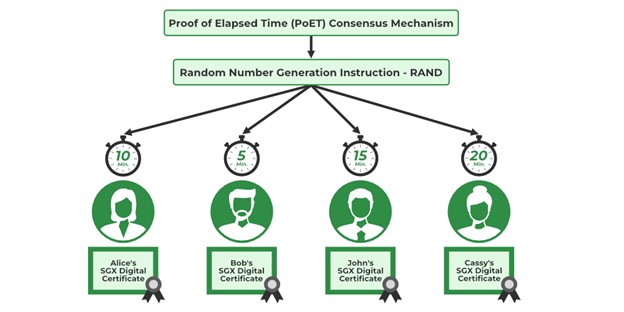
Selection Process
- Each node within the network will provide its Intel Software Guard Extension (SGX) certificate, validating its authority to create a new block. Once certified, the node receives a timer object.
- Intel’s Random Number Generator (RAND) assigns complex, hard-to-predict random numbers to every node.
- The allocated time object triggers a countdown for each participating node upon activation.
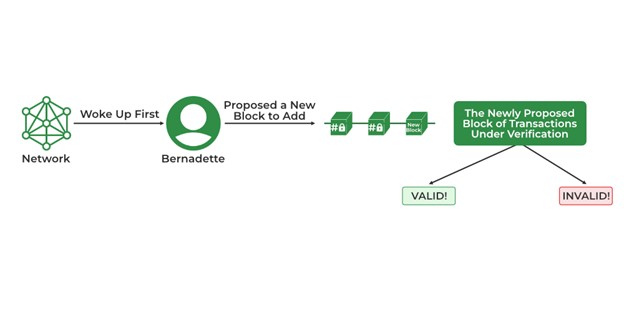
Genesis Process
- Once a node's timer object runs out, the node springs into action and takes on the task of creating a fresh block for the network.
- The active node calculates the hash of its transaction block and sends it for verification.
- Upon successful validation, the revised information is shared across the entire network.
Advantages and Limitations of PoET
Despite its aim to enhance the Proof of Work (PoW) model, PoET is not without its flaws. Similar to other methods, PoET has its own set of advantages and limitations.
Advantages
- Energy Efficiency: PoET stands out for its energy efficiency, eliminating the need for energy-intensive cryptographic puzzle mining, unlike PoW. This aligns with the global shift towards sustainable and eco-friendly blockchain technologies.
- Decentralization: PoET ensures a level playing field for all participants, irrespective of their computational power or capital investment, fostering true decentralization. Unlike PoW, where computational power matters, PoET promotes fairness among nodes.
- Scalability: PoET's efficient and predictable block creation process enhances scalability, allowing for processing a higher number of transactions within a given timeframe.
Limitations
- Permissioned Network: PoET operates exclusively within closed, permissioned networks, which restricts its accessibility compared to open networks like Bitcoin and Ethereum.
- Specialized Hardware Requirement: Implementing PoET requires specific hardware, making it inaccessible to everyone due to the specialized equipment requirements.
- Compatibility Issues: PoET relies heavily on Intel Technology's tools, which might lead to compatibility problems with other software, limiting its seamless integration.
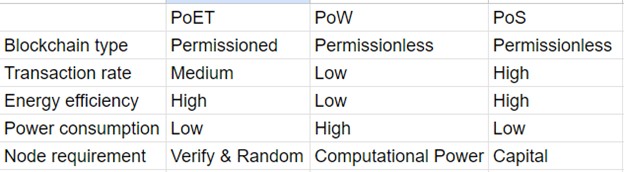
PoET vs PoW vs PoS
While all three are consensus mechanisms utilized in distributed ledgers, PoET distinguishes itself significantly from PoW and PoS. Here's a brief comparison between these methods.
Conclusion
What is Proof of Elapsed Time (PoET)? Proof of Elapsed Time (PoET) stands out as a groundbreaking consensus mechanism, distinct from widely-known methods like Proof of Work (PoW) and Proof of Stake (PoS). PoET finds its ideal application in permissioned (private) blockchains, where participants are meticulously chosen and trusted, obviating the need for intricate trust validation methods.
At the core of PoET lie principles of fairness and energy efficiency. Each network node is assigned a random waiting time, ensuring an equal opportunity to win the chance to create a new block. This fairness is assured by Intel SGX (Software Guard Extensions), which issues certificates to nodes and confirms their operation within a secure, trusted code environment.
While PoET offers numerous advantages, such as energy efficiency, decentralization, and scalability, it does come with certain limitations. It's tailored for permissioned networks, necessitates specialized hardware, and may encounter compatibility issues with other tools.
Here at U2U Chain, we employ PoET as one of our three consensus mechanisms within our "Triple Layer Protection Mechanism," significantly enhancing our chain's performance and security through its distinctive features. Please stay tuned to U2U for more valuable updates on blockchain technology.