Secure blockchain networks are fundamental to the digital landscape, providing decentralized and transparent systems for secure transactions and data storage across industries. As the value of digital assets and sensitive data stored on these networks increases, ensuring the security of blockchain networks becomes paramount. Breaches can lead to devastating financial loss, data theft, and irreparable reputational damage, highlighting the critical need for stringent security protocols. By fortifying secure blockchain networks, we not only protect assets and data but also cultivate trust and encourage broader adoption of blockchain technology in the rapidly evolving digital economy.
Table of Contents
Secure Blockchain Networks
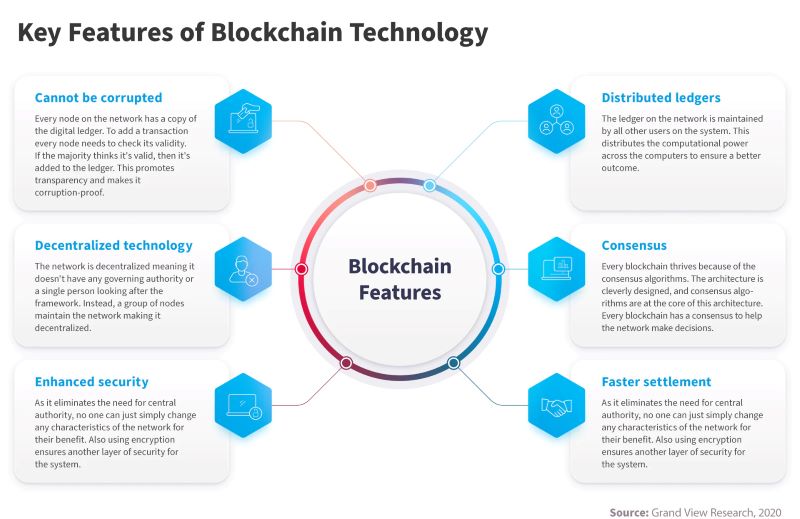
Blockchain technology operates on fundamental principles that ensure its security and reliability in digital transactions. Decentralization, immutability, and cryptographic hashing are core pillars that underpin its robustness. Decentralization distributes transaction verification across a network of nodes, eliminating single points of failure and reducing the risk of manipulation or censorship. Immutability ensures that once data is recorded on the blockchain, it cannot be altered or deleted without consensus from the network participants. Cryptographic hashing secures data integrity by converting transactional inputs into fixed-length strings, making it virtually impossible to reverse-engineer original data from the hash.

Despite these strengths, blockchain networks face various security threats. 51% attacks occur when an entity gains majority control of a blockchain network's computing power, enabling them to manipulate transactions. Sybil attacks involve creating multiple fake identities to gain control over a network. Smart contract vulnerabilities can lead to exploits and funds being drained from decentralized applications (dApps). Social engineering attacks target human vulnerabilities to deceive users into disclosing sensitive information or performing unauthorized actions.
To mitigate these risks, blockchain security employs a "defense in depth" strategy. This approach involves implementing multiple layers of security measures, including robust cryptographic algorithms, consensus mechanisms, secure coding practices for smart contracts, regular audits, and continuous monitoring. Each layer acts as a barrier to protect against different types of threats, ensuring comprehensive defense against potential attacks.
Key Security Measures for Blockchain Networks
The security of blockchain networks is paramount for safeguarding digital assets and ensuring trust in decentralized transactions. Several foundational measures are essential to maintain the integrity, confidentiality, and availability of blockchain data and transactions:
Cryptography
Public-key cryptography: Essential for blockchain security, each user possesses a public key (used for receiving funds) and a private key (used for transaction authorization). The secure relationship between these keys ensures only the rightful owner can initiate transactions.
Hash functions: These generate unique fingerprints (hashes) for blockchain data blocks. Even slight changes in data result in vastly different hashes, making tampering virtually impossible without detection.
Digital signatures: Utilized to verify transaction authenticity, digital signatures are created with the sender's private key and verified using their public key, ensuring only authorized transactions proceed.
Consensus Mechanisms
Proof of Work (PoW): Miners solve complex mathematical problems to add new blocks, ensuring network integrity through computational effort and energy consumption.
Proof of Stake (PoS): Validators are chosen based on the amount of cryptocurrency they hold and are willing to stake as collateral, offering a more energy-efficient alternative to PoW.
Delegated Proof of Stake (DPoS): Token holders vote for delegates responsible for validating transactions and maintaining blockchain consensus.
Smart Contract Security
Code Audits: Rigorous reviews of smart contract code by experienced developers to identify vulnerabilities and potential exploits before deployment.
Formal Verification: Mathematical validation of smart contract behavior against intended specifications to ensure correctness.
Secure Development Frameworks: Adoption of trusted frameworks and libraries that undergo thorough security testing and validation.
Network Security
Firewalls: Control and monitor incoming and outgoing network traffic to prevent unauthorized access to blockchain infrastructure.
Intrusion Detection Systems (IDS): Monitor network activity for suspicious behavior, promptly identifying and mitigating potential threats.
Secure Communication Protocols: Implementation of encrypted protocols (e.g., SSL/TLS) to protect data transmitted between blockchain nodes.
Key Management:
Hardware Wallets: Physical devices storing private keys offline, offering robust protection against cyber attacks and theft.
Multi-Signature Schemes: Require multiple private keys to authorize transactions, enhancing security by distributing trust among multiple parties.
Best Practices: Regularly back up private keys, use strong passwords, and avoid sharing private key information to maintain security integrity.
The Future of Secure Blockchain Networks
As blockchain technology continues to evolve, ensuring robust security measures is crucial to maintaining trust and safeguarding digital assets. Looking ahead, several key factors will shape the future of secure blockchain networks:
Emerging Technologies
Zero-Knowledge Proofs (ZKPs): These cryptographic protocols enable verification of transactions or data without revealing sensitive information. ZKPs enhance privacy and confidentiality on public blockchains, ensuring secure and transparent transactions.
Secure Multi-Party Computation (MPC): MPC protocols enable multiple parties to compute a function together while keeping their inputs private. This technology has the potential to revolutionize blockchain applications by enabling collaborative data analysis and computations without compromising privacy.

Regulatory Landscape
The regulatory environment surrounding blockchain technology is evolving rapidly, with governments worldwide exploring frameworks to address security, privacy, and compliance concerns. Regulations are increasingly focusing on data protection, identity management, and anti-money laundering (AML) measures, impacting how blockchain projects implement security protocols and interact with users.
Industry Collaboration
Collaboration among blockchain projects, security experts, and regulatory bodies is essential to establish standards and best practices for blockchain security. Industry-wide initiatives and partnerships can foster innovation in security protocols, threat intelligence sharing, and incident response frameworks. Cross-sector collaboration ensures that blockchain technology evolves securely, addressing emerging threats and vulnerabilities effectively.
In the increasingly evolving decentralized world, securing blockchain networks is not just an option but a mandatory requirement. Secure Blockchain Networks play a foundational role in protecting digital assets, ensuring transaction integrity, and reinforcing trust in blockchain technology.
With a combination of robust security measures, advanced technology, and close industry collaboration, we can build a future where Secure Blockchain Networks thrive, unlocking the vast potential of blockchain technology to transform how we interact and transact in the digital world. Follow U2U Network to update the latest information about Blockchain




.png)
